Google subpoena scam: What it looks like and how to avoid it



What is a Google subpoena scam?
The Google subpoena scam is a type of phishing attack where fraudsters impersonate Google to create a false sense of urgency and fear.
Typically, you will receive an email that appears to come from no-reply@google.com, claiming to inform you of a subpoena, a formal legal request. The email will often have a subject line like “Security Alert” or “Notice of Subpoena,” making it seem urgent and legitimate. These scammers prey on your natural concern about legal matters and data privacy, hoping to trigger a reaction.
Inside the email, the scammers falsely claim that Google has been served with a subpoena requiring the company to turn over your account data, such as emails, documents or search history. The email will then urge you to click on a link to view your “case materials.” This link typically leads to a fraudulent website, often hosted on Google Sites, which is designed to look like a genuine Google support page. This added layer of legitimacy can easily trick users into believing the request is real.
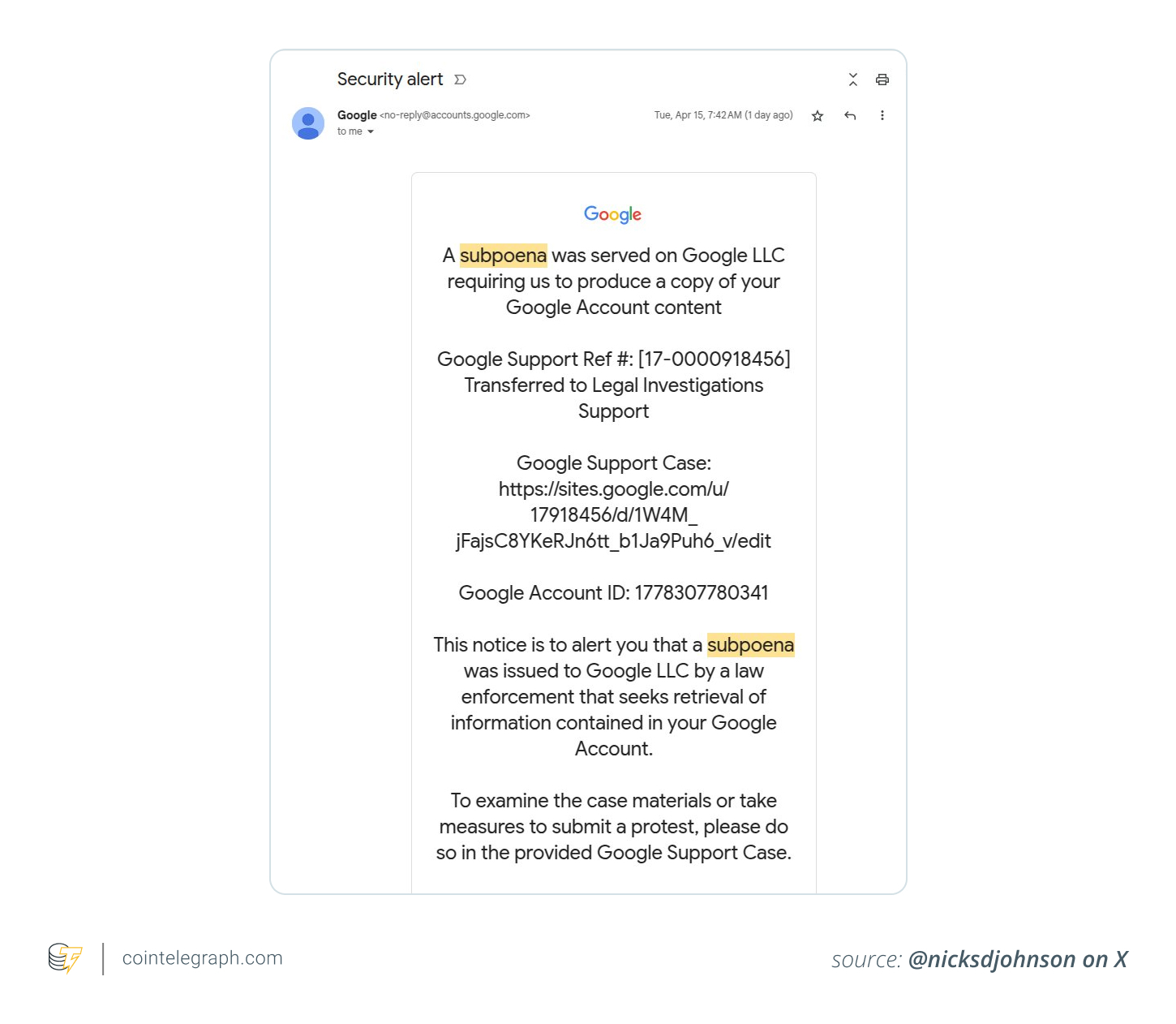
The most concerning part of this scam is that attackers are skilled at spoofing Google’s email addresses and mimicking the company’s official content. By doing so, they can bypass common security checks, such as DomainKeys Identified Mail (DKIM), which normally verifies the authenticity of an email. With this approach, the scam appears convincingly legitimate, making it easy for unsuspecting users to act impulsively — potentially exposing sensitive data or inadvertently installing malware.
Did you know? DomainKeys Identified Mail (DKIM) is an email security standard that verifies whether a message really comes from the domain it claims to be from. It uses cryptographic signatures to protect against email spoofing and phishing attacks — making your inbox just a little safer every day.
How the Google subpoena scam works
Software firm EasyDMARC explained that attackers exploited legitimate Google services to bypass traditional spam filters. They used “OAuth” applications combined with DKIM workarounds to create emails that could fool even careful users.
A DKIM replay attack exploits the way email authentication works, specifically using DomainKeys Identified Mail, which adds a digital signature to an email to verify its authenticity.
Steps of the attack:
- Attacker receives a legitimate Google email: The attacker intercepts a legitimate email from Google that has a valid DKIM signature, which proves it came from Google.
- Preparing the replay: The attacker saves this email, keeping the DKIM signature intact, and replays it. Since DKIM checks only the email headers and body (if unchanged), the attacker can forward the exact email with its signature intact without modification.
- Sending the spoofed email: The attacker then sends this saved email from a different account (e.g., Outlook), making it look like it’s from the original sender (Google).
- Relaying through other servers: The email goes through multiple servers, each adding their own DKIM signature, but the original Google DKIM signature remains untouched and valid.
- Final delivery: The email reaches the victim’s inbox, appearing legitimate. Despite being relayed through several servers, the email passes SPF, DKIM and DMARC checks, which makes it look like a valid Google email.
The result: The victim is tricked into thinking it’s a legitimate message, potentially leading to harmful actions like clicking malicious links or providing sensitive information. This type of attack plays on the trust people place in email authentication methods and shows how attackers can exploit them.
Here’s how fake Google emails and DKIM replay attacks trick you:
- Spoofed Google support pages: Clicking the link in the email takes you to a fake Google support page, often hosted on Google Sites, adding another layer of false credibility. The website will urge you to log in to view your “case materials.”
- Phishing for credentials: If you proceed, you’re asked to enter your Google username and password. Once entered, the attackers can gain full access to your account.
- Psychological tricks: Scammers use fear-based tactics — mentioning lawsuits, law enforcement involvement or threats of account suspension. The urgency they create is designed to make you bypass your usual caution.
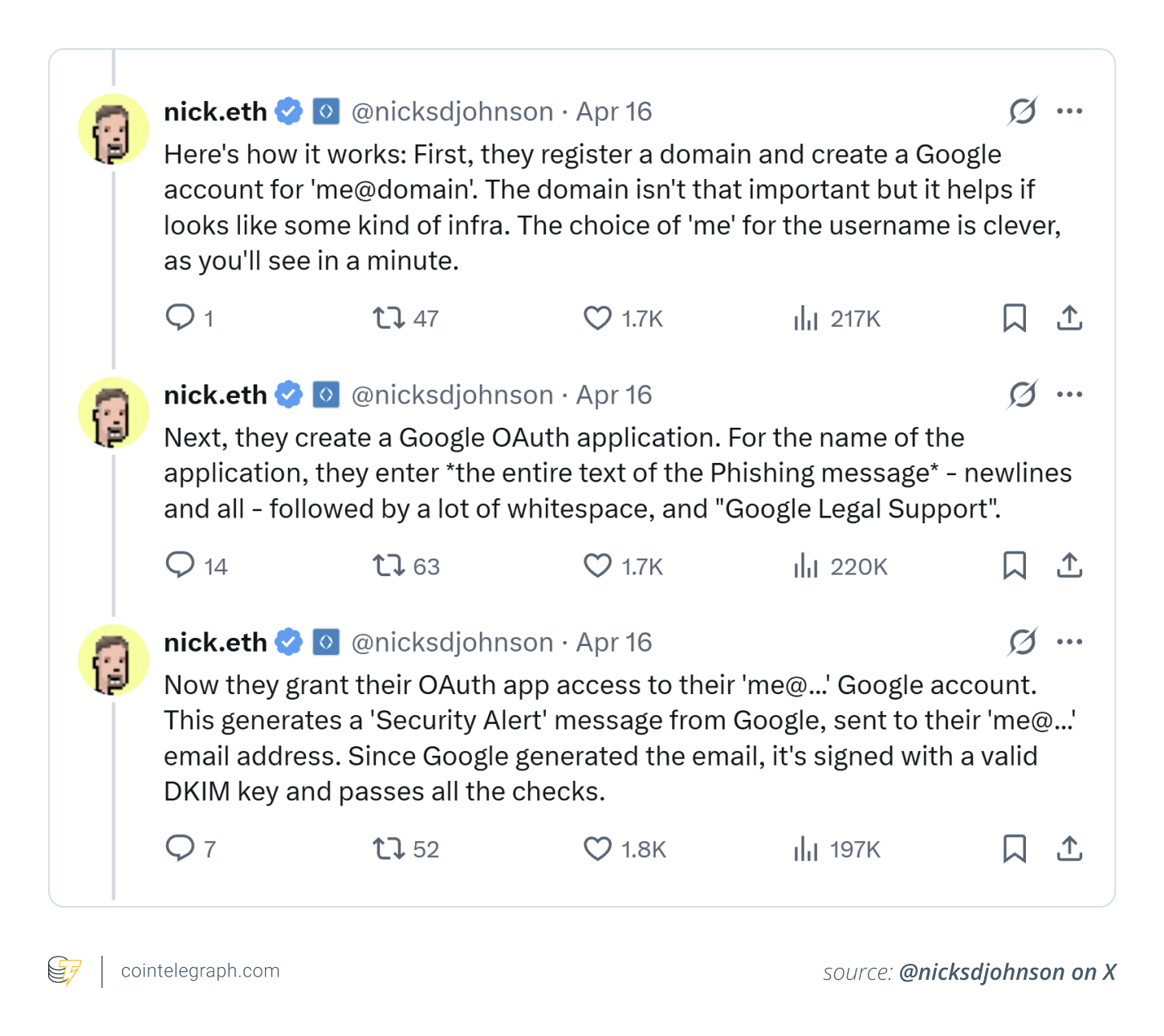
Did you know? Google Sites lets anyone with a Google account create websites under the trusted “sites.google.com” domain. Attackers exploit this by crafting fake login pages and phishing forms, using Google’s SSL and brand reputation to deceive users into revealing sensitive information.
Key signs you’re facing a Google subpoena scam
Even though the Google subpoena scam is highly sophisticated, there are still clear red flags you can look for if you know what to watch out for.
By recognizing these signs, you can protect yourself from falling victim to phishing attacks:
- Fake or spoofed sender addresses: The first thing you should do is examine the sender’s email address carefully. Even though these scams may appear to come from a legitimate Google address, small differences in the sender’s domain or name can indicate that the email is a spoof. For instance, a Google email may have slight alterations, such as “goog1e.com” instead of “google.com,” which are often overlooked by unsuspecting users.
- Urgent language and threats: Scammers will often try to pressure you into acting quickly by using urgent language and threats of legal action. They may claim that your account is at risk of being suspended or that you must act immediately to avoid severe consequences. Google does not use scare tactics like this in emails.
- Requests for sensitive information: One of the biggest signs of a phishing attempt is a request for sensitive information, such as your Google account password, two-factor authentication (2FA) code or personal financial details. Google will never ask for this information via email.
- Poor grammar or formatting: While scammers have gotten better at mimicking official communication, many still make mistakes. Look for inconsistent wording, odd phrasing or formatting errors. These can often reveal a scam.
- Suspicious links: Before clicking any link in an email, hover over it with your mouse to preview the URL. If the link looks suspicious or unfamiliar, don’t click on it. Often, scammers use disguised URLs that lead to fake websites.
- Lack of proper legal process: Real subpoenas are issued through proper legal channels. They are never delivered via an email that asks for personal information or a quick action.
Received a Google subpoena email? Here’s how to stay safe
If you receive an email that claims to be from Google about a legal subpoena or any other suspicious notification, it’s important to remain calm and avoid reacting hastily.
Phishing attacks, like the Google subpoena scam, often rely on creating a sense of urgency to trick users into making mistakes. Here’s what you should do immediately to protect your personal information and accounts:
- Do not click any links: Avoid interacting with the email. Don’t open attachments, click links or reply.
- Verify the request: Visit Google’s support site directly (not through any link in the email) and check if there are any notifications related to your account.
- Report the scam: In the UK, forward the suspicious email to report@phishing.gov.uk or Google’s own reporting channels, and in the US, notify the Federal Trade Commission (FTC) at reportfraud.ftc.gov or forward to spam@uce.gov.
- Update your security settings: Immediately change your Google account password and enable 2FA or passkeys for an extra layer of protection.
- Contact your bank: If you shared any financial details (e.g., credit card numbers, bank account information or payment credentials), act quickly. Call your bank or financial institution using the official number on the back of your card or its verified website. Inform them of the potential scam and any compromised information. Request to monitor your account for suspicious activity, freeze or cancel affected cards, or issue new ones if necessary. Review recent transactions for unauthorized charges and dispute any fraudulent activity promptly.
- Report to authorities: If you believe you have fallen victim, report the incident to Action Fraud or call 101 if you’re based in the UK. File a complaint with the FTC at www.ftc.gov/complaint or report to the Federal Bureau of Investigation’s Internet Crime Complaint Center (IC3) at www.ic3.gov if you are based in the US.
How Google notifies users about legal requests
When it comes to legal requests such as subpoenas, court orders or search warrants, Google takes privacy and security seriously. The company has a strict procedure in place to ensure that requests for user data are valid, lawful and processed through proper channels.
Unlike the tactics employed by scammers, Google’s approach is both transparent and secure. Here’s how the real process works when it comes to legal requests for your data:
- Google checks the request carefully: If law enforcement (e.g., police or court) requests your data, Google thoroughly reviews the request to ensure it’s valid and lawful.
- Google may notify you: Unless they’re not allowed (e.g., due to a court order), Google will let you know before sharing your information. This notice won’t come in a random email asking for your password.
- Official notifications only: If there’s a real legal issue, you’ll see a message in your Google Account dashboard (like in the “Security” section when you log in) or through an official Google email from a verified address, not a suspicious or random one.
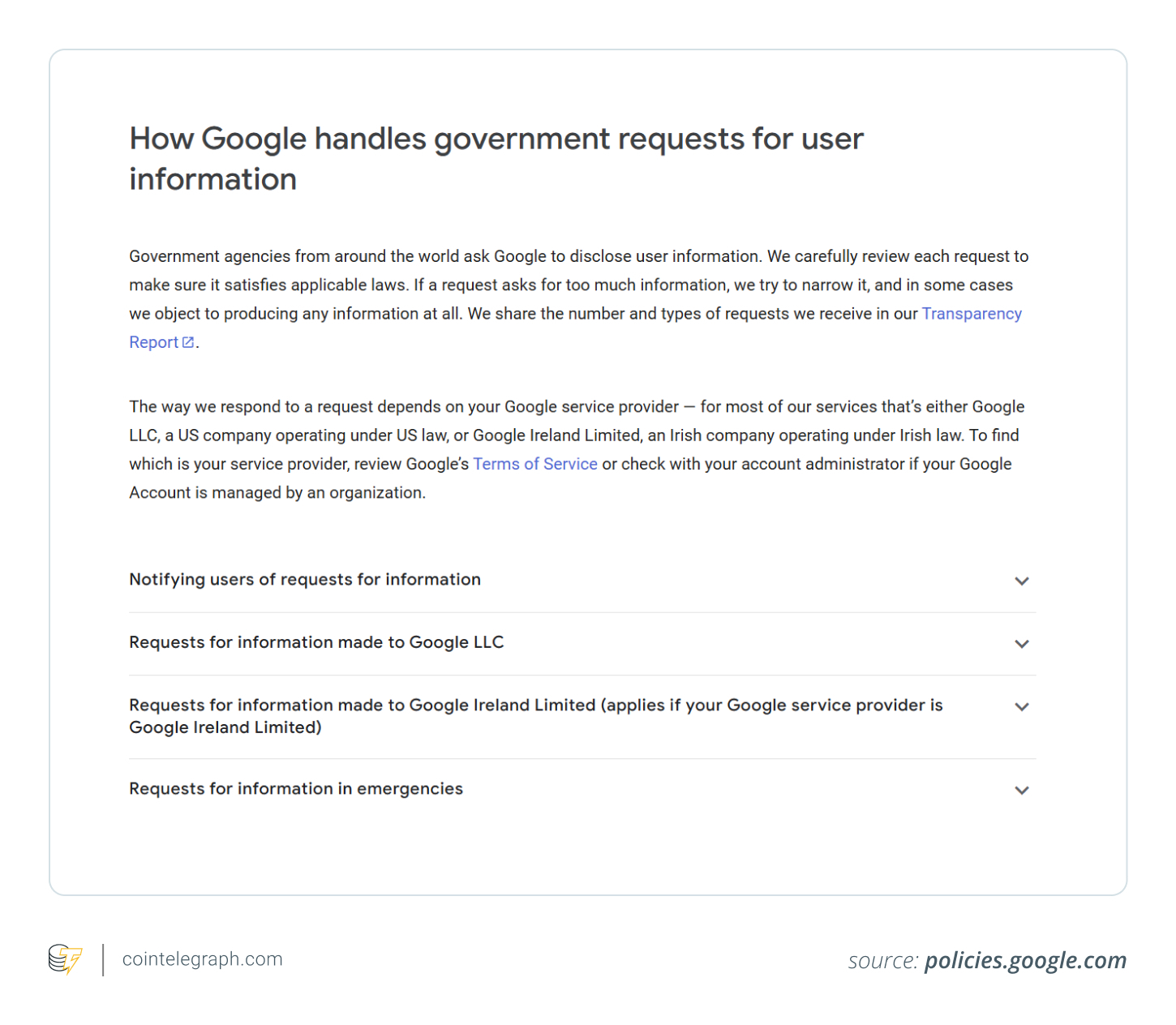
Did you know? Government agencies worldwide request user data from Google, but each request is carefully reviewed to ensure it complies with the law. Google shares details of these requests in its Transparency Report, and how they respond depends on whether your service provider is Google LLC (US) or Google Ireland Limited (Ireland).
How to avoid falling victim to Google subpoena scams
To avoid falling victim to Google subpoena scams, stay calm, avoid clicking any links or attachments, and verify any legal claims directly through Google’s official support channels.
Phishing scams are constantly evolving, but you can significantly reduce your risk by following some best practices, including:
- Stay skeptical: Always question unexpected emails, especially those involving legal action or urgent threats.
- Inspect carefully: Click the dropdown next to the sender’s name to see the full email address and domain.
- Hover before clicking: Hover your cursor over any links to preview the URL without actually clicking.
- Enable 2FA: Adding an extra layer of security to your Google account can stop scammers even if they steal your password.
- Use advanced spam filters: Tools like spam blockers, domain verification tools (like Who.is) and secure email gateways can help flag suspicious emails.
- Regular security audits: Periodically review your Google Account’s security settings and connected third-party apps.
- Stay updated: Subscribe to trusted cybersecurity newsletters or Google’s security updates to stay informed about new threats.
- Educate yourself and others: Sharing knowledge about scams with friends, family and coworkers can help build a collective defense.